Ever wondered How to parse Windows logs? How to parse .evtx/.evt files? How to investigate windows logs? How to create full logs timeline? How to analyse all windows logs at once.
As a forensic analyst, EVTXECmd is a powerful tool for working with Windows Event Log (EVTX) files. It provides various options and functionalities to perform forensic analysis and investigation. Here are some possible options and use cases for EVTXECmd:
1. **Extracting Events**:
EVTXECmd allows you to extract specific events or a range of events from an EVTX file. This can be useful when you want to focus on specific event IDs or timeframes relevant to your investigation.
2. **Filtering Events**:
You can apply filters based on event properties such as Event ID, keywords, provider name, time range, etc. Filtering helps to narrow down the event log data and focus on specific events of interest.
3. **Converting EVTX to CSV**:
EVTXECmd provides the ability to convert EVTX files into a more human-readable format like CSV. This makes it easier to analyze and process the event log data using other tools or scripts.
4. **Searching for Keywords**:
You can search for specific keywords or patterns within the event log data using EVTXECmd. This helps in identifying events related to specific activities or indicators of compromise (IOCs).
5. **Timeline Creation**:
EVTXECmd allows you to create a timeline of events based on their timestamps. This can help in establishing a sequence of events and understanding the chronological order of activities.
6. **Identifying Event Log Tampering**:
EVTXECmd can detect and report any inconsistencies or tampering in the event log file. It can verify the integrity of the EVTX file and identify any modifications or deletions.
7. **Parsing Event Metadata**:
EVTXECmd provides options to extract and analyze metadata associated with events, such as event descriptions, source IPs, usernames, etc. This can assist in understanding the context of events and identifying potential malicious activities.
8. **Comparing Event Logs**:
You can compare multiple EVTX files using EVTXECmd to identify differences or similarities in event log data. This can be helpful in detecting anomalies or identifying changes between different systems or timeframes.
9. **Exporting Event Logs**:
EVTXECmd allows you to export event log data into various formats, including JSON, XML, and CSV. This enables easy integration with other tools or platforms for further analysis or reporting.
10. **Analyzing Security Events**:
EVTXECmd provides specific options to analyze security-related events, such as authentication failures, privilege escalations, network connections, and other security-related activities. This helps in identifying potential security incidents or unauthorized access attempts.
Remember to refer to the EVTXECmd documentation or help menu for detailed usage instructions and command syntax.
How to install and use evtxecmd
Install full suite of forensics tools offered by Eric Zimmerman’s, why it will be easier to update all of them in one click, and easier to manage
- Visit: https://ericzimmerman.github.io/#!index.md and click on get eric Zimmerman’s tool
- Extract this .zip file there is Get-ZimmermanTools.ps1 file.
- First bypass the execution policy to execute this file.
- PS E:\Eric zimmerman tools> Set-ExecutionPolicy Bypass.
- Then execute PS E:\Eric zimmerman tools> .\Get-ZimmermanTools.ps1
Once done it will show like this:
- The following files are created in the installation directory.
- Installation completed
- How to parse Windows events/.evtx files (both on the running system or collected from other systems)
- You might get this error while executing
- Error: You must install .NET to run this application
- Learn about runtime installation: https://aka.ms/dotnet/app-launch-failed
- Download the .NET runtime.
- Now goto the https://dotnet.microsoft.com/en-us/download/dotnet/6.0
- Once the installation is completed.
- Re-run the tool.
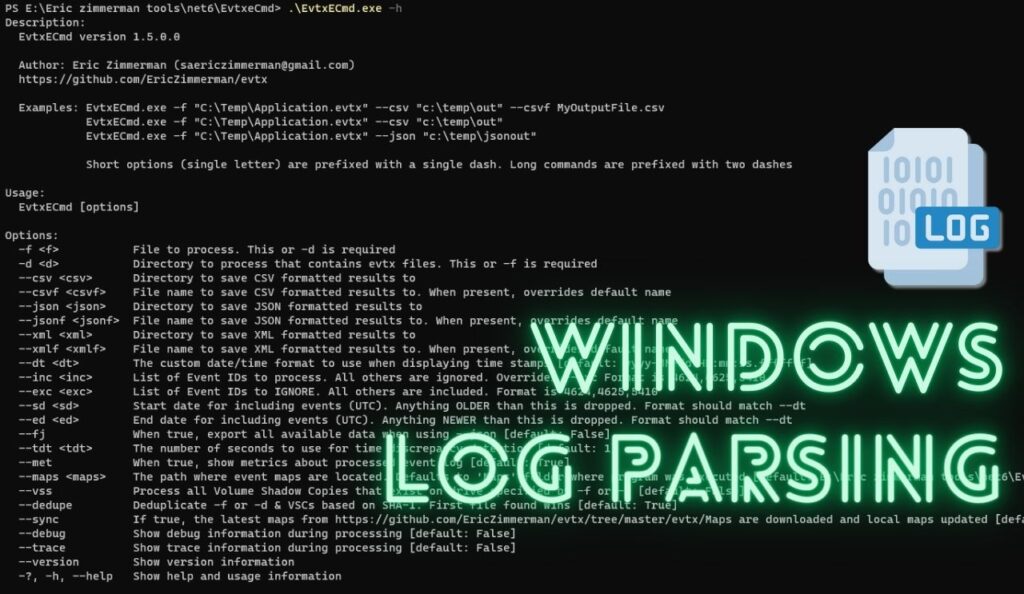
- PS E:\Eric zimmerman tools\net6\EvtxeCmd> .\EvtxECmd.exe -h
Before using the tool lets understand what is “maps”
- The `–maps` option in EVTXECmd generates mapping files in CSV format.
- These mapping files provide human-readable interpretations of numeric values found in EVT files.
- Numeric values in EVT files can include event IDs, task names, opcode names, and other contextual information.
- The mapping files associate numeric values with their corresponding human-readable interpretations.
- The mappings help in understanding the meaning and significance of numeric values in EVT files.
- Mapping files for event IDs may include event names, descriptions, and event sources.
- The `–maps` option enhances the readability and comprehensibility of EVT files during forensic analysis.
- It provides valuable context and aids in correlating and understanding log data.
- The mapping files facilitate efficient analysis and improve the effectiveness of forensic examinations.
Use the following command to update the maps:
- PS E:\Eric zimmerman tools\net6\EvtxeCmd> .\EvtxECmd.exe –sync
As you can see maps are not only for Windows native logs files but also for the apps installed on systems like CiscoSecureEndpoint, and Kaspersky-security, which can be found under System>Provider name logs or might have their own log channel.
Another option you want to look at:
- –vss – Process all Volume Shadow Copies that exist on drive specified by -f or -d
The `–vss` option in EVTXECmd is used to process Event Log files from Volume Shadow Copies. Here’s an expansion on its functionality:
- Volume Shadow Copies (VSS) are snapshots of a file system at a specific point in time, allowing the recovery of files as they appeared at that moment.
- The `–vss` option enables EVTXECmd to access and analyze Event Log files within VSS.
- By using this option, EVTXECmd can examine Event Logs from different timeframes, allowing forensic analysts to review logs from specific points in the past.
- VSS copies can provide valuable insight into system activity, especially in cases where logs may have been altered or deleted in the live system.
- The `–vss` option allows for the recovery and analysis of Event Log files that were present in the VSS snapshots.
- Analysts can compare and contrast Event Logs from different VSS copies to identify changes, anomalies, or potential evidence of malicious activity.
- It is important to note that the VSS feature must be enabled on the system and have available snapshots for EVTXECmd to access and analyze.
- It enhances the ability to recover and analyze Event Logs from specific points in time, expanding the forensic capabilities of EVTXECmd.
Run the tool:
- EvtxECmd.exe -d C:\Windows\System32\winevt\Logs –csv “E:\Eric zimmerman tools\net6\EvtxeCmd\Parsed logs” –csvf ConsolidatedParsedlogs.csv –vss
Explanation:
The command `EvtxECmd.exe -d C:\Windows\System32\winevt\Logs –csv “E:\Eric zimmerman tools\net6\EvtxeCmd\Parsed logs” –csvf ConsolidatedParsedlogs.csv –vss` performs the following actions with the `–vss` option included:
- The `EvtxECmd.exe` command invokes the EVTXECmd tool for processing Event Log files.
- The `-d C:\Windows\System32\winevt\Logs` argument specifies the source directory where the original Event Log files are located. In this case, it points to the default Event Log location in the Windows directory.
- The `–csv “E:\Eric zimmerman tools\net6\EvtxeCmd\Parsed logs“` argument specifies the destination directory where the parsed logs will be saved. The tool will convert the Event Log files to CSV format and store them in this directory.
- The `–csvf ConsolidatedParsedlogs.csv` argument specifies the filename for the consolidated CSV file that will contain all the parsed logs. In this case, the filename is set as “ConsolidatedParsedlogs.csv“.
- The `–vss` option indicates that the tool should also process Event Log files from Volume Shadow Copies (VSS).
- By including `–vss`, EVTXECmd will analyze Event Log files from both the original source directory and any available Volume Shadow Copies.
- This allows for a comprehensive analysis of Event Logs from different timeframes, increasing the chances of detecting and investigating potential security incidents.
- The `–vss` option is particularly useful in forensic investigations where historical event data from VSS snapshots is required for analysis or incident response.
- By including this option, the command ensures that Event Log files from VSS are considered during the processing and consolidation into the final CSV output file.
- Here Flags: Isdirty (means the file is in use)
See the output folder:
How to open this file:
If you want to use excel for this its fine, but if you don’t have Excel or want to use a new tool, the great option we have available as a forensics analyst is “TimelineExplorer.exe” in the same Eric Zimmerman tools directory: E:\Eric zimmerman tools\net6\TimelineExplorer
Here we have all the parsed logs