Understanding What a DDoS Attack Is
A Distributed Denial of Service (DDoS) attack is when multiple sources flood a website or online service with so much traffic that it can’t cope, causing slowdowns or complete shutdown. This attack uses a network of compromised computers, known as a botnet, to send an overwhelming number of requests to the target, effectively blocking legitimate users from accessing the service. DDoS attacks are used for various reasons, such as disrupting services or extortion, and defending against them involves robust cybersecurity measures like firewalls and specialized anti-DDoS software.
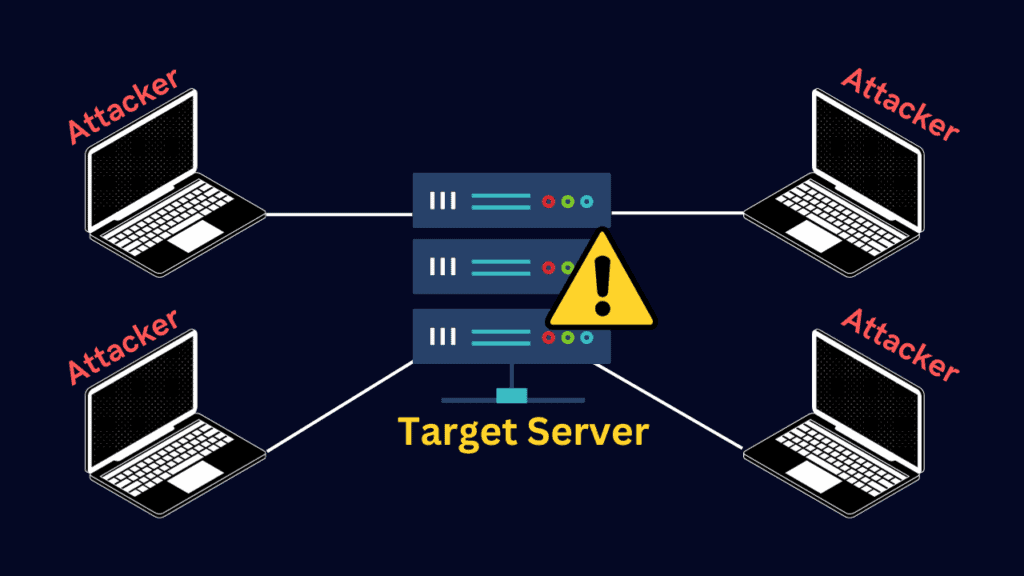
Identifying the Signs of a DDoS Attack
- Website speed drastically drops.
- Site crashes repeatedly.
- Unusual traffic spikes occur.
- Specific services become unavailable.
- User access is sporadically blocked.
- Connection timeouts increase.
- Cybersecurity tools trigger warnings.
Responding Effectively During a DDoS Attack
- Immediate Activation of Response Plan: Quickly implementing your pre-defined response plan is crucial.
- Engagement with ISP and DDoS Mitigation Services: Collaboration with your ISP and third-party DDoS mitigation services can provide additional support and resources.
- Traffic Analysis and Response Adjustment: Continuously monitor traffic to identify the attack’s nature and adjust your defensive tactics accordingly.
Post-Attack Analysis and Recovery Strategies
here are the key steps for post-attack analysis and recovery strategies:
1. Assess and contain the attack.
2. Document the incident.
3. Communicate and report to stakeholders.
4. Investigate the attack forensically.
5. Eradicate the threat and recover systems.
6. Patch and update vulnerabilities.
7. Improve security measures.
8. Train users on security awareness.
9. Implement continuous monitoring.
10. Review and revise your incident response plan.
11. Ensure legal and regulatory compliance.
12. Manage public relations and reputation.
13. Learn from the incident and document lessons.
14. Continuously monitor and adapt security measures.
15. Conduct regular incident simulation and preparedness testing.
Conclusion: Building a Resilient Online Defense
In conclusion, while DDoS attacks are a significant threat in the digital world, understanding and preparing for them can greatly enhance your resilience. By adopting these strategies and maintaining vigilance, you can ensure the safety and continuity of your online presence.