Summary of the Blog
- Understanding System Hacking:
- How System Hacking Occurs:
- How to Protect Against System Hacking:
Understanding System Hacking:
System hacking is the unauthorized intrusion into computer systems, networks, or devices to compromise their integrity, confidentiality, or availability. While it may sound malicious, it’s important to understand that learning about system hacking improves cybersecurity defenses.
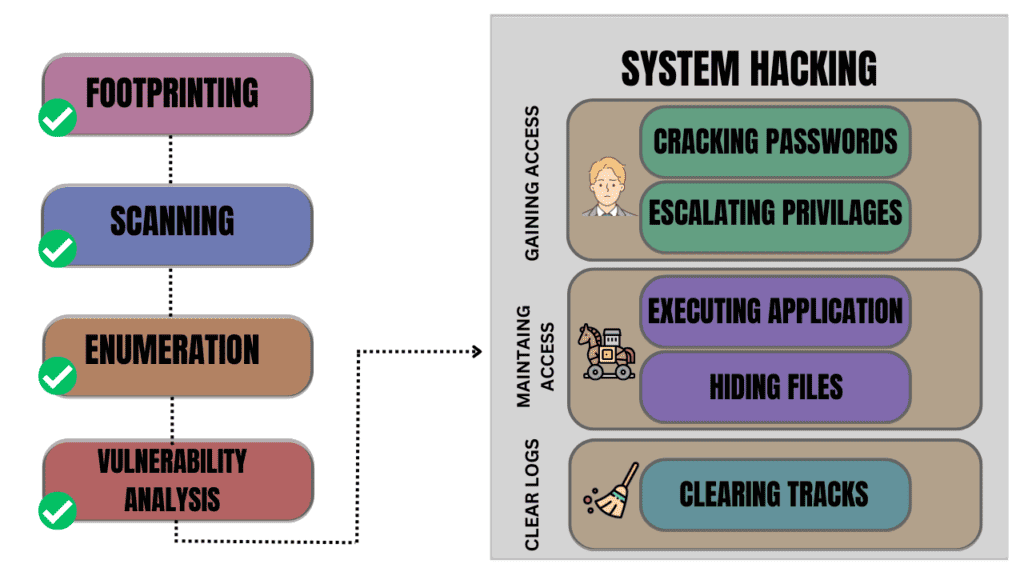
How System Hacking Occurs:
1 . Identifying Vulnerabilities:
Hackers start by identifying vulnerabilities in the target system, which may result from unpatched security flaws, outdated software, and misconfigurations.
2 . Reconnaissance:
Before launching an attack, hackers conduct reconnaissance to gather information about the target. This phase involves studying the target’s infrastructure, network topology, and potential entry points.
3 . Exploitation:
With knowledge, hackers exploit vulnerabilities by using malware, unsecured protocols, and other techniques to gain access.
4 . Privilege Escalation:
After gaining initial access, hackers often try to escalate their privileges within the system to gain higher-level control over critical components.
5 . Maintaining Access:
To ensure prolonged access, hackers often create backdoors or other persistent mechanisms that allow them to re-enter a system even after it has been detected and removed.
How to Protect Against System Hacking:
- Regular Software Updates:
It is important to keep all software and operating systems up-to-date to protect against known exploits and patch vulnerabilities.
2 . Firewalls and Intrusion Detection Systems:
Deploy firewalls and intrusion detection systems to monitor and control network traffic, detecting and preventing unauthorized access.
3 . Secure Authentication Practices:
Implement multi-factor authentication to increase security and prevent unauthorized access.
5 . Employee Training:
Educate employees on identifying phishing and avoiding social engineering attacks, highlighting security best practices.
6 . Network Segmentation:
Segmenting networks can limit the lateral movement of attackers, reducing the impact of intrusion.
Conclusion
As technology advances, so too do the skills of those who seek to exploit its vulnerabilities. Acknowledging the existence of system hacking is a critical step in building a robust defense against potential threats. By adopting proactive cybersecurity measures and fostering a culture of awareness, individuals and organizations can safeguard their digital assets from the shadows that lurk in the ever-expanding realm of cyberspace. It is through knowledge, vigilance, and collective effort that we can navigate the digital landscape securely and protect against the risks of system hacking.